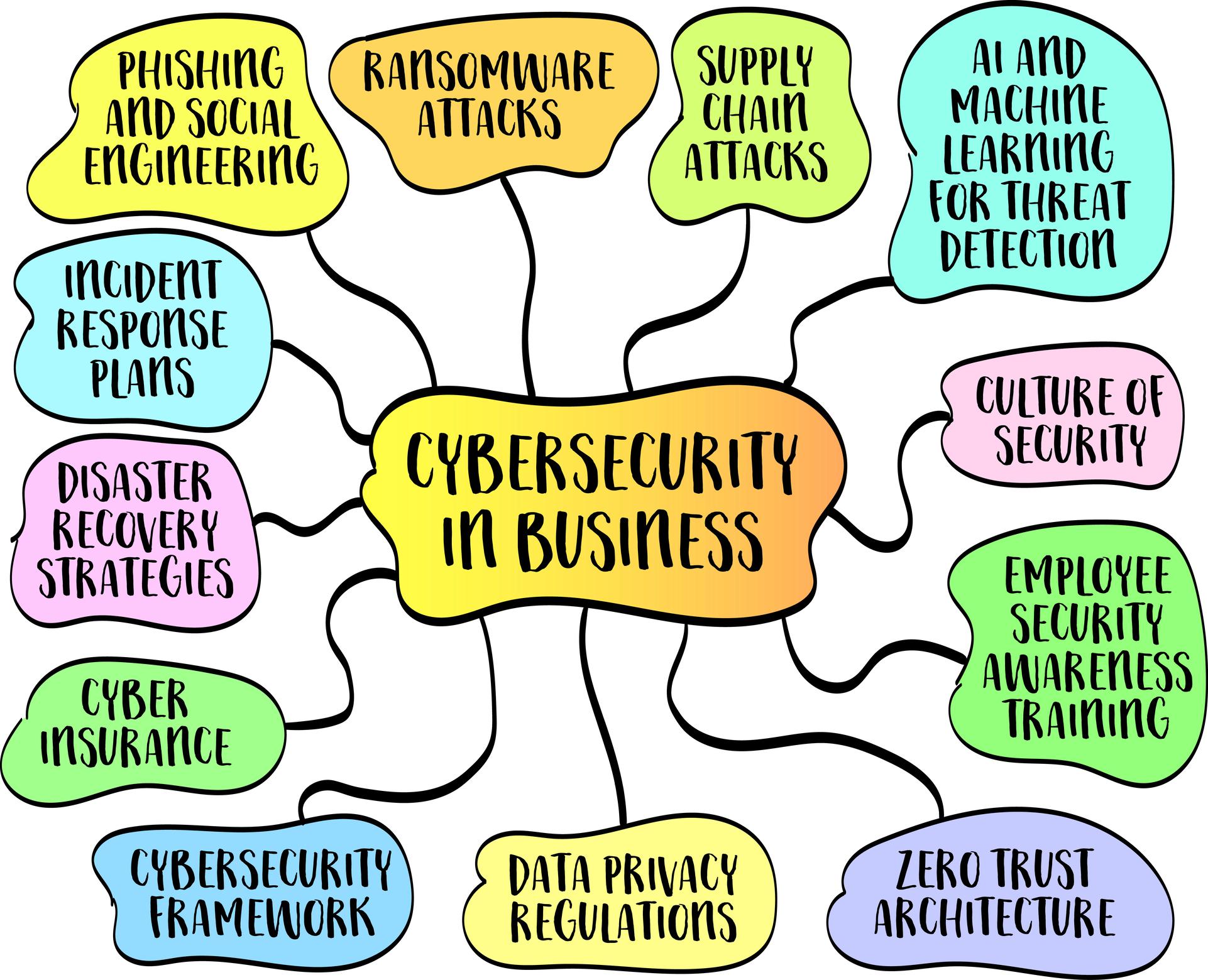
Cybersecurity
Protecting Your Most Valuable Assets
In today's interconnected world, cybersecurity is not just an IT concern—it's a critical business imperative. At Jacob Meadow Associates LLC, we understand that your data, systems, and reputation are your most valuable assets. We partner with you to build a robust cybersecurity posture that protects your business from evolving threats.
Our Cybersecurity Services
- Cybersecurity Strategy & Risk Assessment: We work with you to develop a comprehensive cybersecurity strategy that aligns with your business objectives and risk tolerance. We conduct thorough risk assessments to identify vulnerabilities and prioritize mitigation efforts.
- Security Architecture & Design: We design and implement security solutions that are tailored to your specific needs, ensuring your data and systems are protected at all levels.
- Incident Response & Recovery: We help you prepare for, respond to, and recover from security incidents, minimizing downtime and mitigating damage.
- Security Awareness Training: We educate your employees on best practices and empower them to be your first line of defense against cyber threats.
- Ongoing Monitoring & Management: We provide continuous monitoring and management of your security infrastructure to detect and respond to threats in real time.
Benefits for Your Business
- Protection of Sensitive Data: Safeguard your customer data, intellectual property, and financial information from unauthorized access and breaches.
- Business Continuity: Minimize downtime and ensure uninterrupted operations in the face of cyberattacks.
- Enhanced Reputation: Demonstrate your commitment to security and build trust with your customers and partners.
- Regulatory Compliance: Stay ahead of evolving regulations and avoid costly penalties.
- Peace of Mind: Focus on your core business with confidence, knowing that your cybersecurity is in expert hands.
Safeguard your business from cyber threats. Contact us today to learn how we can help you build a resilient cybersecurity posture.